Important Things to Check:
- Active Processes
- Terminal Commands
- Hidden Proccesses
- Browser History
do lab0 first, its an amazingly detailed introduction to get you started!
Lab 1: Beginner’s Luck#
My sister’s computer crashed. We were very fortunate to recover this memory dump. Your job is get all her important files from the system. From what we remember, we suddenly saw a black window pop up with some thing being executed. When the crash happened, she was trying to draw something. Thats all we remember from the time of crash.
points to note:
- “suddenly saw a black window”: check out console history
- “trying to draw something”: mspaint
Console History#
❯ ../vol -f MemoryDump_Lab1.raw --profile=Win7SP1x64 consoles
Volatility Foundation Volatility Framework 2.6
**************************************************
CommandHistory: 0x1fe9c0 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 1 LastAdded: 0 LastDisplayed: 0
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x60
Cmd #0 at 0x1de3c0: St4G3$1
----
Screen 0x1e0f70 X:80 Y:300
Dump:
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Users\SmartNet>St4G3$1
ZmxhZ3t0aDFzXzFzX3RoM18xc3Rfc3Q0ZzMhIX0=
Press any key to continue . . .gives us the first flag flag{w3lc0m3_T0_$T4g3_!_Of_L4B_2}
Active Processes#
The important processes to note are below
❯ ../vol -f MemoryDump_Lab1.raw --profile=Win7SP1x64 pslist
Volatility Foundation Volatility Framework 2.6
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit
------------------ -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------
0xfffffa8002222780 cmd.exe 1984 604 1 21 1 0 2019-12-11 14:34:54 UTC+0000
0xfffffa80022bab30 mspaint.exe 2424 604 6 128 1 0 2019-12-11 14:35:14 UTC+0000
0xfffffa8001010b30 WinRAR.exe 1512 2504 6 207 2 0 2019-12-11 14:37:23 UTC+0000MS Paint#
Lets dump the all memory associated with MSPaint. Since it’s probably a graphic of some sort let’s open it with GIMP. Messing with the scale a little finally gives us this
❯ ../vol -f MemoryDump_Lab1.raw --profile=Win7SP1x64 memdump -D dump -p 2424
Volatility Foundation Volatility Framework 2.6
************************************************************************
Writing mspaint.exe [ 2424] to 2424.dmp
Giving us the 2nd flag flag{Go0d_BoY_good_girl_}
WinRAR.exe#
Since WinRAR is open, perhaps there is a .rar archive somewhere containing something for us
❯ ../vol -f MemoryDump_Lab1.raw --profile=Win7SP1x64 filescan > files.txt
❯ cat files.txt | rg "\.rar"
0x000000003fa3ebc0 1 0 R--r-- \Device\HarddiskVolume2\Users\Alissa Simpson\Documents\Important.rar
0x000000003fac3bc0 1 0 R--r-- \Device\HarddiskVolume2\Users\Alissa Simpson\Documents\Important.rar
0x000000003fb48bc0 1 0 R--r-- \Device\HarddiskVolume2\Users\Alissa Simpson\Documents\Important.raromg an Important.rar, let’s extract it with
❯ ../vol -f MemoryDump_Lab1.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000003fa3ebc0 -D dump/
Volatility Foundation Volatility Framework 2.6
DataSectionObject 0x3fa3ebc0 None \Device\HarddiskVolume2\Users\Alissa Simpson\Documents\Important.rar❯ unrar v file.None.0xfffffa8001034450.dat
UNRAR 7.13 freeware Copyright (c) 1993-2025 Alexander Roshal
Archive comment:
Password is NTLM hash(in uppercase) of Alissa's account passwd.
Archive: file.None.0xfffffa8001034450.dat
Details: RAR 5
Attributes Size Packed Ratio Date Time Checksum Name
----------- --------- -------- ----- ---------- ----- -------- ----
* ..A.... 46045 41856 90% 2019-12-11 19:04 997C37CD flag3.png
----------- --------- -------- ----- ---------- ----- -------- ----
46045 41856 90% 1well lets get our hash and find our final flag!
../vol -f MemoryDump_Lab1.raw --profile=Win7SP1x64 hashdump
Volatility Foundation Volatility Framework 2.6
Alissa Simpson:1003:aad3b435b51404eeaad3b435b51404ee:f4ff64c8baac57d22f22edc681055ba6:::
Our 3rd and final flag is flag{w3ll_3rd_stage_was_easy}
Lab 2: A New World#
One of the clients of our company, lost the access to his system due to an unknown error. He is supposedly a very popular “environmental” activist. As a part of the investigation, he told us that his go to applications are browsers, his password managers etc. We hope that you can dig into this memory dump and find his important stuff and give it back to us.
points to note:
- “environmental”: check envars
- “browsers”: check browser history
- “password managers”: look for an installed password manager
Environment Variables#
❯ ../vol -f MemoryDump_Lab2.raw --profile=Win7SP1x64 envars > dump/envA simple scan through this file shows me a NEW_TMP envar
NEW_TMP C:\Windows\ZmxhZ3t3M2xjMG0zX1QwXyRUNGczXyFfT2ZfTDRCXzJ9which gives us the first flag: flag{w3lc0m3_T0_$T4g3_!_Of_L4B_2}
Password Managers#
Let’s look for an installed password manager
❯ ../vol -f MemoryDump_Lab2.raw --profile=Win7SP1x64 filescan > dump/file_scan❯ cat dump/file_scan | rg -e "Downloads"
0x000000003fa218f0 14 0 R--r-d \Device\HarddiskVolume2\Users\SmartNet\Downloads\winrar-x64-580.exe
0x000000003fb465d0 15 0 R--r-d \Device\HarddiskVolume2\Users\SmartNet\Downloads\KeePass-2.43-Setup.exe
0x000000003fb93780 2 1 R--rwd \Device\HarddiskVolume2\Users\SmartNet\Downloads\DumpItWe can see KeePass-2.43-Setup.exe. Let’s for files related to it
❯ cat dump/file_scan | rg -e "KeePass"
0x000000003e8be8e0 16 0 R--r-- \Device\HarddiskVolume2\Users\Alissa Simpson\AppData\Roaming\KeePass\KeePass.config.xml
0x000000003e8c8070 16 0 R--r-- \Device\HarddiskVolume2\Users\SmartNet\AppData\Roaming\KeePass\KeePass.config.xmlThe .xml files look like they might contain something interesting, since I couldn’t see any .db files.
❯ ../vol -f MemoryDump_Lab2.raw --profile=Win7SP1x64 dumpfiles -p 1632 --dump-dir dump/ -Q 0x000000003e8be8e0here’s an interesting entry
<DatabasePath>..\..\Users\SmartNet\Secrets\Hidden.kdbx</DatabasePath>I extracted the file but it was password protected and I couldn’t crack it. I found this lovely writeup by the same guy who who made this lab lmao. I couldn’t find the password in the memory dump either though :(
Taking a little hint from a writeup
❯ cat dump/file_scan | rg -ie "password"
0x000000003fce1c70 1 0 R--r-d \Device\HarddiskVolume2\Users\Alissa Simpson\Pictures\Password.pngInteresting. The password is P4SSw0rd_123
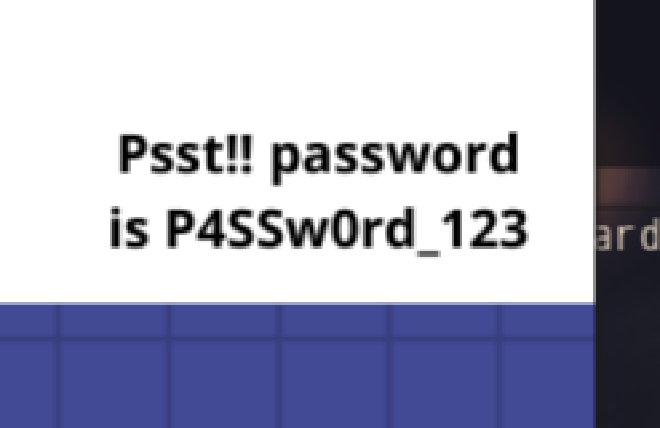
Now we can download KeePassXC to open up Hidden.kdbx with the password to get the second stage flag flag{w0w_th1s_1s_Th3_SeC0nD_ST4g3_!!}
Browser History#
Chrome Artifacts:
❯ cat dump/file_scan | rg -e "Chrome\\\User Data\\\Default\\\History"
0x000000003fcfb1d0 18 1 RW-rw- \Device\HarddiskVolume2\Users\SmartNet\AppData\Local\Google\Chrome\User Data\Default\Historychrome stores user history in the History file which is a sqlite3 database. We can dump it and analyse it as
❯ ../vol -f MemoryDump_Lab2.raw --profile=Win7SP1x64 dumpfiles -p 1632 --dump-dir dump/ -Q 0x000000003fcfb1d0
❯ sqlite3 dump/file.None.0xfffffa8000efd1d0.datsqlite> SELECT * FROM urls;
9|https://volatilevirus.home.blog/|Abhiram's Blog – Dying Is The Day Worth Living For!!|1|1|13220789251877522|0
11|https://r3xnation.wordpress.com/|R3xNation – Free Flowing passions|1|1|13220789357212089|0
13|https://ashutosh1206.github.io/|Home | Ashutosh|1|1|13220789373876790|0
28|http://blog.bi0s.in/|bi0s|1|0|13220790112269568|0
32|https://mega.nz/#F!TrgSQQTS!H0ZrUzF0B-ZKNM3y9E76lg|MEGA|2|0|13220792499602970|0Some of the notable urls from history, the mega.nz looks particularly tempting! Visiting the link gives us an Important.zip file to download
❯ file dump/Important.zip
dump/Important.zip: Zip archive data, at least v2.0 to extract, compression method=AES Encrypted❯ unzip dump/Important.zip
Archive: dump/Important.zip
Password is SHA1(stage-3-FLAG) from Lab-1. Password is in lowercase.
skipping: Important.png unsupported compression method 99We can compute the required hash to get 6045dd90029719a039fd2d2ebcca718439dd100a and thus we get the 3rd flag
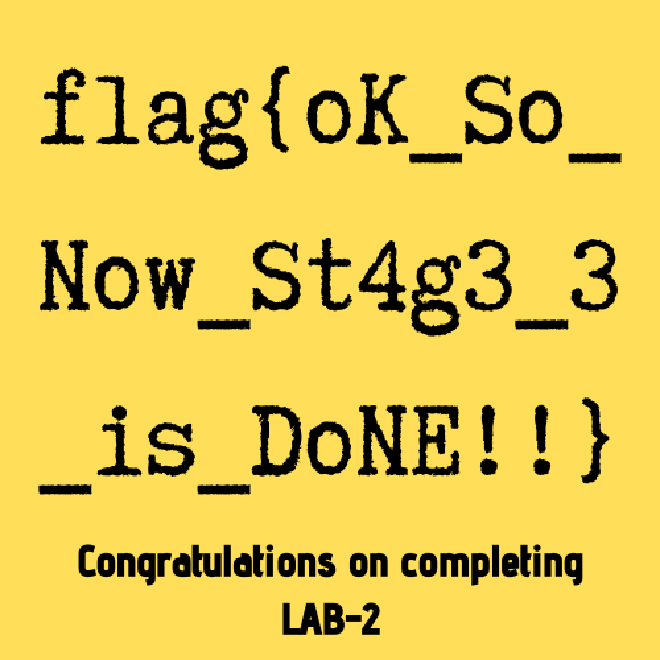
flag{oK_So_Now_St4g3_3_is_DoNE!!}
Lab 3: The Evil’s Den#
A malicious script encrypted a very secret piece of information I had on my system. Can you recover the information for me please?
points to note:
- “malicious script”: we’re looking for a script, that could be
.bat,.py,.sh, let’s see - we’re going to be reverse engineering the script to decrypt the data
Malicious Script#
The user’s \Desktop folder contains the files we need, that was easy!
❯ cat dump/file_scan | rg -ie "hello\\\Desktop"
0x0000000004f34148 2 \Users\hello\Desktop\suspision1.jpeg
0x00000000385d3958 8 \Users\hello\Desktop\OSForensics.lnk
0x000000003d3c0f80 1 \Users\hello\Desktop\DumpIt\HELLO-PC-20180930-094543.raw
0x000000003dcf3f18 8 \Users\hello\Desktop\DumpIt\DumpIt.exe
0x000000003de1b5f0 8 \Users\hello\Desktop\evilscript.py.py
0x000000003de41d00 8 \Users\hello\Desktop\desktop.ini
0x000000003e727e50 8 \Users\hello\Desktop\vip.txt | |
and the text in vip.txt is “am1gd2V4M20wXGs3b2U=”. Simply reversing this xor we get the first part of the flag inctf{0n3_h4lf
Steganography#
There’s another interesting file in the \Desktop folder, let’s see if we can find anything in there
The lab description suggested using steghide. So using steghide on the suspision1.jpeg with the first part of the flag as the passphrase, we get the embedded secret text file which contains the second part of the flag
❯ steghide extract -sf suspision1.jpeg -p inctf{0n3_h4lf
❯ cat secret\ text
_1s_n0t_3n0ugh}With that we get the flag inctf{0n3_h4lf_1s_n0t_3n0ugh}
Lab 4: Obsession#
My system was recently compromised. The Hacker stole a lot of information but he also deleted a very important file of mine. I have no idea on how to recover it. The only evidence we have, at this point of time is this memory dump. Please help me.
points to note:
- recover deleted files
File Scan#
Since we’re looking for files we start by dumping the filelist and searching for files of note there
❯ ../vol -f MemoryDump_Lab4.raw --profile=Win7SP1x64 filescan > dump/file_scan
❯ cat dump/file_scan | rg -e "Desktop"
0x000000003e8ad250 14 0 R--r-- \Users\eminem\Desktop\galf.jpeg
0x000000003e8d19e0 16 0 R--r-- \Users\eminem\Desktop\Screenshot1.png
0x000000003fc398d0 16 0 R--rw- \Users\SlimShady\Desktop\Important.txtdumping galf.jpeg and Screenshot1.png didn’t lead to anything, in fact galf.jpeg was just a red herring with a LMAO.txt embedded in it. So next we go to Important.txt. Dumping it with dumpfiles doesn’t actually give anything though, so this must be the deleted file we need to recover.
MFT Parse#
The MFT is the Master File Table of the NTFS file system which is the default file system of Windows systems. It contains all details about the files and their metadata, stored as attributes.
We can dump the MFT with Volatility
❯ ../vol -f MemoryDump_Lab4.raw --profile=Win7SP1x64 mftparser > dump/mft_scanand look for the entry of Important.txt
$FILE_NAME
Creation Modified MFT Altered Access Date Name/Path
------------------------------ ------------------------------ ------------------------------ ------------------------------ ---------
2019-06-27 13:14:13 UTC+0000 2019-06-27 13:14:13 UTC+0000 2019-06-27 13:14:13 UTC+0000 2019-06-27 13:14:13 UTC+0000 Users\SlimShady\Desktop\Important.txt
$OBJECT_ID
Object ID: 7726a550-d498-e911-9cc1-0800275e72bc
Birth Volume ID: 80000000-b800-0000-0000-180000000100
Birth Object ID: 99000000-1800-0000-690d-0a0d0a0d0a6e
Birth Domain ID: 0d0a0d0a-0d0a-6374-0d0a-0d0a0d0a0d0a
$DATA
0000000000: 69 0d 0a 0d 0a 0d 0a 6e 0d 0a 0d 0a 0d 0a 63 74 i......n......ct
0000000010: 0d 0a 0d 0a 0d 0a 0d 0a 66 7b 31 0d 0a 0d 0a 0d ........f{1.....
0000000020: 0a 5f 69 73 0d 0a 0d 0a 0d 0a 5f 6e 30 74 0d 0a ._is......_n0t..
0000000030: 0d 0a 0d 0a 0d 0a 5f 45 51 75 34 6c 0d 0a 0d 0a ......_EQu4l....
0000000040: 0d 0a 0d 0a 5f 37 6f 5f 32 5f 62 55 74 0d 0a 0d ...._7o_2_bUt...
0000000050: 0a 0d 0a 0d 0a 0d 0a 0d 0a 0d 0a 5f 74 68 31 73 ..........._th1s
0000000060: 5f 64 30 73 33 6e 74 0d 0a 0d 0a 0d 0a 0d 0a 5f _d0s3nt........_
0000000070: 6d 34 6b 65 0d 0a 0d 0a 0d 0a 5f 73 33 6e 0d 0a m4ke......_s3n..
0000000080: 0d 0a 0d 0a 0d 0a 73 33 7d 0d 0a 0d 0a 47 6f 6f ......s3}....Goo
0000000090: 64 20 77 6f 72 6b 20 3a 50 d.work.:PFor small text files often their contents are stored in the $DATA attribute of their MFT entry, and here we can see the flag, albeit with a lot of whitespace characters
We can clean it up a little to get the flag: inctf{1_is_n0t_EQu4l_7o_2_bUt_th1s_d0s3nt_m4ke_s3ns3}
Lab 5: Black Tuesday#
We received this memory dump from our client recently. Someone accessed his system when he was not there and he found some rather strange files being accessed. Find those files and they might be useful. I quote his exact statement,
The names were not readable. They were composed of alphabets and numbers but I wasn’t able to make out what exactly it was.
Also, he noticed his most loved application that he always used crashed every time he ran it. Was it a virus?
points to note:
- look for strange files
- check the “most used” application
- look for viruses
Strange Files#
We’re looking for “strange files” so let’s start by dumping the files list. Some common places to try can be \Desktop, \Downloads, etc. However I didn’t see anything of note there, so I moved on to looking for browser history.
Internet Explorer History#
We can use the iehistory plugin!!! Alternatively we could use the screenshot plugin which would show us a wireframe image of the windows that were open at the time of the memdump
❯ ../vol -f MemoryDump_Lab5.raw --profile=Win7SP1x64 iehistory
Volatility Foundation Volatility Framework 2.6
**************************************************
Process: 1396 explorer.exe
Cache type "DEST" at 0x635910f
Last modified: 2019-12-20 09:16:37 UTC+0000
Last accessed: 2019-12-20 03:46:38 UTC+0000
URL: Alissa Simpson@file:///C:/Windows/AppPatch/ZmxhZ3shIV93M0xMX2QwbjNfU3Q0ZzMtMV8wZl9MNEJfNV9EMG4zXyEhfQ.bmpinteresting looking file name: flag{!!_w3LL_d0n3_St4g3-1_0f_L4B_5_D0n3_!!}
WinRAR.exe#
Feeling lost once again, let’s go through the processes
❯ ../vol -f MemoryDump_Lab5.raw --profile=Win7SP1x64 pslist
Volatility Foundation Volatility Framework 2.6
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit
------------------ -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------
0xfffffa8000f97a20 WinRAR.exe 2924 1580 6 210 2 0 2019-12-20 03:47:13 UTC+0000
0xfffffa800221ab30 NOTEPAD.EXE 1388 1580 1 39 2 1 2019-12-20 03:48:00 UTC+0000
0xfffffa8000efbb30 WerFault.exe 780 2632 7 160 2 1 2019-12-20 03:48:01 UTC+0000We can use the cmdline plugin to see what file WinRAR.exe was run on
❯ ../vol -f MemoryDump_Lab5.raw --profile=Win7SP1x64 cmdline
Volatility Foundation Volatility Framework 2.6
************************************************************************
WinRAR.exe pid: 2924
Command line : "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\SmartNet\Documents\SW1wb3J0YW50.rar"
********************************************************************************************
NOTEPAD.EXE pid: 2724
Command line : "C:\Users\SmartNet\Videos\NOTEPAD.EXE"
****************************************************************************************************************************we can dump SW1wb3J0YW50.rar and extract it with the first flag as the password to get the second flag
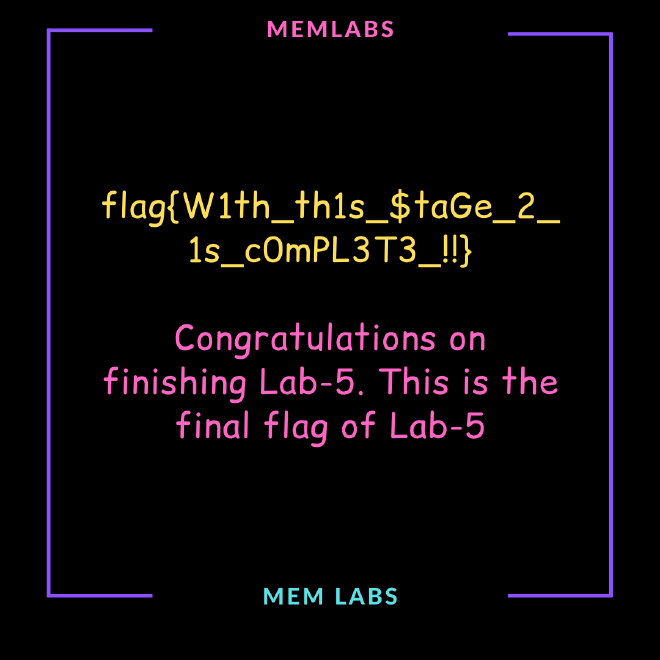
giving us the second flag flag{W1th_th1s_$taGe_2_1s_c0mPL3T3_!!}
Virus???#
in the pslist above we can see a NOTEPAD.exe that is followed by WerFault.exe. WerFault.exe is run when an app crashes so we can be sure this is process to analyse. We can also from cmdline see that NOTEPAD.exe comes from C:\Users\SmartNet\Videos\NOTEPAD.EXE which is NOT a system path, sooo…
Since this is supposed to be “a virus”, let’s dump it analyse what it’s doing
A short detour to discuss the PE32 file format, which is basically the windows ELF file and the file format of NOTEPAD.exe. PE files contain an optional header that includes a lot of their attributes. I’ve opened our file in Binary Ninja
struct PE32_Optional_Header __pe32_optional_header =
{
enum pe_magic magic = PE_32BIT;
uint8_t majorLinkerVersion = 0x7;
uint8_t minorLinkerVersion = 0xa;
uint32_t sizeOfCode = 0x7800;
uint32_t sizeOfInitializedData = 0xa600;
uint32_t sizeOfUninitializedData = 0x0;
uint32_t addressOfEntryPoint = 0x739d;
uint32_t baseOfCode = 0x1000;
uint32_t baseOfData = 0x9000;
uint32_t imageBase = 0x1000000;
uint32_t sectionAlignment = 0x1000;
uint32_t fileAlignment = 0x200;
uint16_t majorOperatingSystemVersion = 0x5;
/* more stuff */
}The addressOfEntryPoint is the relative offset of our entry point and to get it’s virtual address we need to add the imageBase address to it, giving us 0x100739d. If we navigate to that address in binja, we get the _WinMainCRTStartup() function
void _WinMainCRTStartup()
/* some stuff */
int32_t esi_1 = *__acmdln
int32_t var_24 = esi_1
bool cond:0 = *esi_1 != 0x22
int32_t var_d8
__builtin_memcpy(dest: &var_d8, src: U"}!_ReVO_5B4l_m3M{s0ib", count: 0x54)
/* some stuff */
}That’s an interesting looking memcpy there, giving us our 3rd flag: bi0s{M3m_l4B5_OVeR_!}
Lab 6: The Reckoning#
We received this memory dump from the Intelligence Bureau Department. They say this evidence might hold some secrets of the underworld gangster David Benjamin. This memory dump was taken from one of his workers whom the FBI busted earlier this week. Your job is to go through the memory dump and see if you can figure something out. FBI also says that David communicated with his workers via the internet so that might be a good place to start.
points to note:
- internet
WinRAR#
easypeasyvirus aN_Am4zINg_!igU3Ss???}
Chrome History#
https://pastebin.com/RSGSi1hk https://mega.nz/file/SrxQxYTQ
Key#
❯ strings MemoryDump_Lab6.raw | rg -i "The key is"
THE KEY IS zyWxCjCYYSEMA-hZe552qWVXiPwa5TecODbjnsscMIUCheck out the Cryptonite writeup for good detail
Reply by Email